Information:
Due to the necessary security measures in certificate handling since macOS Catalina (10.15), it may happen that a Mac cannot access Swyx Desktop for Mac OS via the Remote Connector or a local SwyxWare after updating to macOS Catalina.
This can occur with self-signed certificates as SwyxWare can generate and also with issued certificates of a public certification authority.
The necessary parameters a certificate must have are explained by Apple on this page:
https://support.apple.com/de-de/HT210176
Important: This refers exclusively to the certificates used for public access to port 9101 (Web service authentication endpoint) and Port 9100 (RestAPI Full).
The certificates existing on the clients (SwyxIt! client) or the Swyx-Mobile clients or MacOS client do NOT have to be reissued because they are not affected by the change listed here!
*** Please do not modify other Certificates ***
These certificates (see administration manual) can be an own certificate and does not have to correspond to the certificate used by SwyxWare to generate the certificates for remote connector access. If no own certificate is used, the certificate used in the Config Wizard will be used (either self-signed by SwyxWare or a public signed certificate).
If a public certificate is used, which corresponds to the above information from Apple, no changes on SwyxWare are necessary.
If no own certificate is used, a valid certificate according to the Apple guidelines can be generated with the following steps.
Run "netsh http show sslcert" to print a list of the certificates and the respective ports. The relevant bindings are to port 9101 and 9100
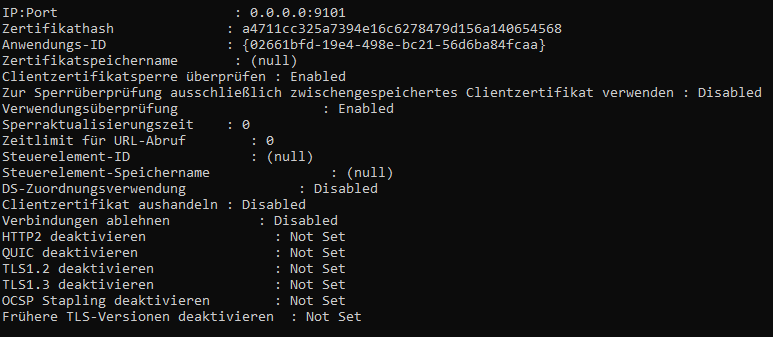
For the next steps we need the values certificate hash (a4711....54568) und Application ID (026.....fcaa)
- Select Run from the Start menu, and then enter certlm.msc.
The Certificate Manager tool for the local device appears. - Expand the Personal/Certificates folder to show a list of the local certificates
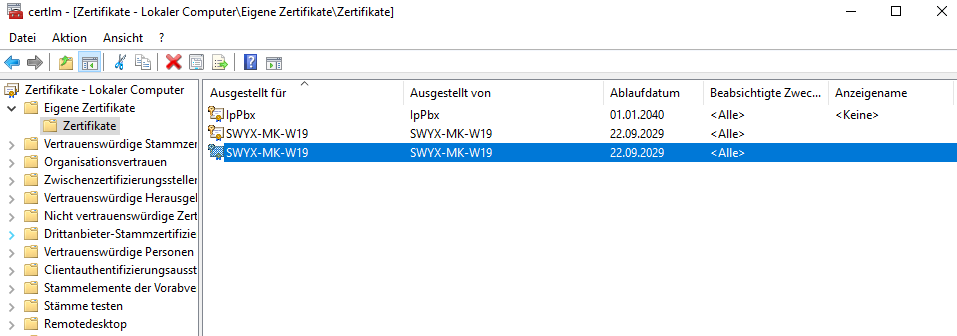
- Double-click one of the elements with "Issued To" equals the server host name ('SWYX-MK-W19' in this example) and select Details/Show: Properties Only
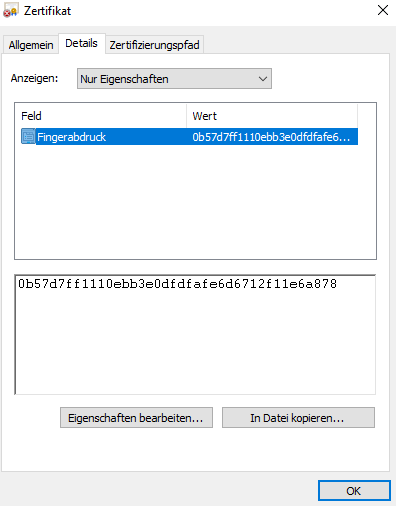
- If the "Thumbprint" value matches the "Certificate Hash" value from step 1. the correct certificate is selected
- To create a new certificate to match the requirements we need to lookup the host FQDN and the remote connector FQDN
Retrieve the host FQDN via powershell
[System.Net.Dns]::GetHostByName(($env:computerName))The value "HostName" will provide the FQDN needed
The remote connector FQDN is shown by SwyxWare Administration by Properties/RemoteConnector/Authentication Server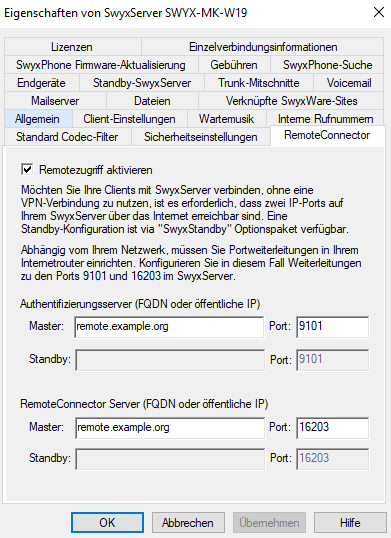
- By this information a new certificate can be created with the following powershell commands.
In order to be able to connect independently of IP address (if no local DNS server is available) as well as names, it is advisable to also list the IP addresses in the SAN (Subject Alternative Names).
If you are using a Microsoft Windows Server 2012 r2, Powershell does not yet understand the term "-notAfter". Therefore, please use the following entry (the certificate is valid for 1 year):> $todaydt = Get-Date> $ValidUntil = $todaydt.AddDays(800)> New-SelfSignedCertificate -DnsName "<host FQDN>","<remote connector FQDN>", "local IP-Address", "Public IP-Address" -notafter $ValidUntil -CertStoreLocation cert:\LocalMachine\My
> New-SelfSignedCertificate -DnsName "<host FQDN>","<remote connector FQDN>", "public IP-Address", "local IP-Address" -CertStoreLocation cert:\LocalMachine\My - If the new certificate was created a summary including the thumbprint is shown
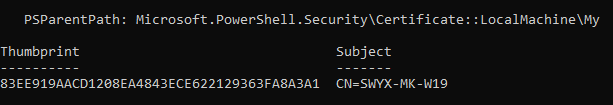
- Additional hint: a list of the certificates with thumbprint and subject can be shown by the command "ls Cert:\LocalMachine\My\"
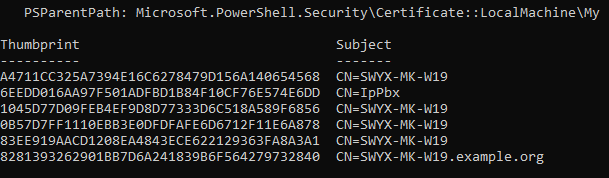
- The current certificate must be detached and the newly created certificate must be bound to the port
Run "netsh http delete sslcert 0.0.0.0:9101" to detach the current certificate from port
> netsh http delete sslcert 0.0.0.0:9101
SSL Certificate successfully deleted - Attach new certificate to port with application ID from step 1 and thumbprint from creation output
83EE919AACD1208EA4843ECE622129363FA8A3A1
netsh http add sslcert ipport=0.0.0.0:9101 certhash=83EE919AACD1208EA4843ECE622129363FA8A3A1 appid="{02661bfd-19e4-498e-bc21-56d6ba84fcaa}"
Das SSL-Zertifikat wurde erfolgreich hinzugefügt. - Confirm binding the certificate to port by repeating step 1
netsh http show sslcert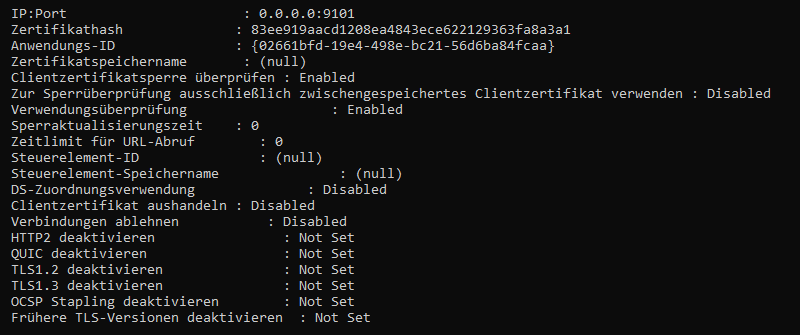
Please do the same steps again for Port 9100. Keep in mind and doublecheck that you use the correct AppID and CertificateHash for this port.
Now Swyx Desktop for Mac OS clients on a macOS with Catalina should be able to connect to Catalina again without problems.

Comments
0 comments
Article is closed for comments.